What's the fuzz about NIS2?
In short, the 10 Most Important Key Requirements in NIS 2
- Cybersecurity Risk Assessments and Policies: Organizations must regularly conduct risk assessments and implement comprehensive security policies to identify, evaluate, and mitigate cyber threats.
- Incident Reporting and Notification: Significant cybersecurity incidents must be reported to national authorities within 24 hours for early warning and a full report within 72 hours, followed by a final report within one month.
- Senior Management Accountability: Executive leadership is directly responsible for cybersecurity compliance, including oversight, approval of strategies, and undergoing regular cybersecurity training.
- Business Continuity and Disaster Recovery: Entities must develop and maintain business continuity plans, including robust backup and recovery procedures, to ensure resilience during and after cyber incidents.
- Incident Handling and Response Framework: A structured incident response plan must be in place, including detection, management, and recovery processes for security breaches.
- Supply Chain Security Management: Organizations must assess and ensure the cybersecurity posture of third-party vendors and suppliers, integrating security requirements into procurement and contracts.
- State-of-the-art (up to date) security must in place in relation to risks
Sensitive data must be encrypted both in storage and during transmission, with cryptographic policies in place to prevent unauthorized access. - Access Control and Asset Management: Strict access control policies, including multi-factor authentication and continuous authentication measures, must be implemented to protect critical assets.
- Cybersecurity Awareness and Training: All employees, including management, must receive regular cybersecurity awareness training to reduce risks related to human error and foster a security-first culture2345.
- Continuous Monitoring and Security Audits: Organizations are required to continuously monitor systems, conduct regular security audits, penetration tests, and evaluate the effectiveness of security measures to ensure ongoing compliance. Security is not a 1-off setting.
These requirements form the backbone of NIS 2 compliance, aiming to strengthen cyber resilience, minimize risks, and ensure rapid response and recovery from security incidents across the EU.
How does NIS2 impact me as company or SMB?
The NIS2 Directive will have a significant impact on companies across the EU, both as direct operators and as suppliers as well.
Organizations classified as “essential” or “important” entities—such as those in energy, healthcare, transportation, ICT, manufacturing, and digital services—must implement stricter cybersecurity measures, conduct detailed risk assessments, and comply with uniform incident notification obligations.
Management teams will be held directly accountable for cybersecurity failures, and non-compliance could result in substantial fines of up to €10 million or 2% of annual turnover for essential entities. The scope of NIS2 is broader than its predecessor, covering not only large organizations but also those whose disruption could significantly impact public safety or the economy, regardless of size.
Indirectly, the NIS2 Directive places new demands on suppliers, especially those providing IT products and services or operating within critical supply chains.
Companies must now identify and rigorously assess their critical suppliers, as any vulnerabilities in the supply chain could jeopardize compliance and operational resilience.
Suppliers will face heightened scrutiny, with increased expectations for cybersecurity standards and risk management practices. This shift means that even businesses not directly regulated by NIS2 may need to enhance their cybersecurity posture to maintain contracts with regulated entities, making robust supply chain security a strategic imperative for all organizations involved.
In many ways the NIS2 is similar to GDPR for data protection, and they are linked to each other. A cyber incidents always comes with data protection issues.
One way or another, you’ll be impacted by NIS2.
CyberFundamentals workshop & assessment: where are you?
The Center for Cybersecurity Belgium (CCB) unveiled its Cyberfundamentals framework to boost cybersecurity among Belgian businesses.
This framework is valuable for both Belgian and international companies operating under NIS 2, directly or indirectly as supplier.
As the Cyberfundamentals provided strong and helpful guidance with practical tools, it’s a interesting starter towards cyber-resilience and compliance.
Where are you?
Our skilled experts will guide your through the NIS2 and Cyberfundamentals and can provide an assessment to measure your readiness?
What is the Cyberfundamentals Framework?
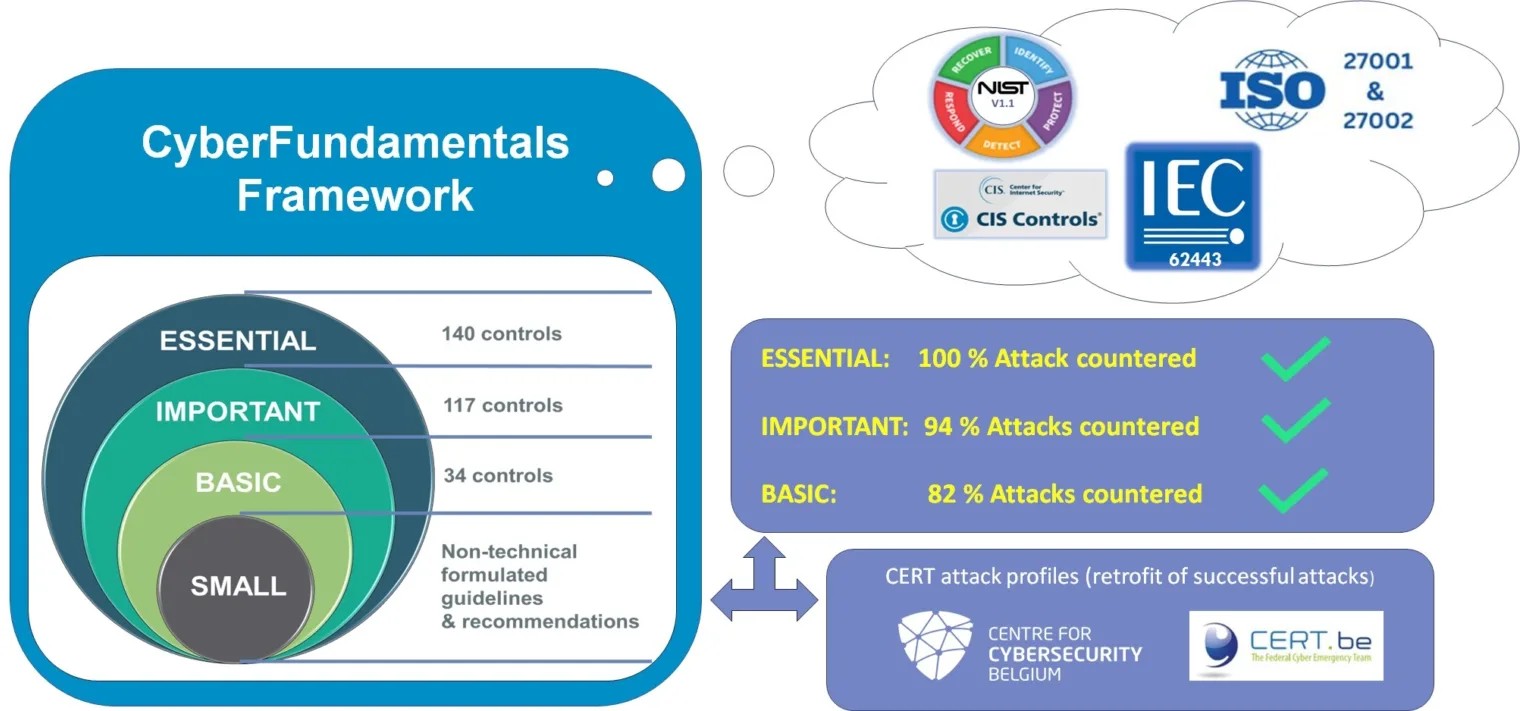
The Belgian Cyberfundamentals framework provides a set of requirements designed to enhance cybersecurity within your company. It includes specific measures to reduce the risks of common cyberattacks, aligning with established frameworks such as NIST CSF, ISO 27001 / ISO 27002, CIS Controls, and IEC 62443.
Like the NIST CSF, the framework’s measures are categorized into five core functions: identify, protect, detect, respond, and recover. Each function includes measures derived from the NIST CSF, supplemented with insights from other frameworks, reviewed by industry experts, and validated against real-world cyberattack data.
Check it out at https://cyfun.be
How Can I Apply CyFun in My Company?
The Cyberfundamentals framework is structured into different levels of measures:
- Small: For micro-organizations or startups, covering the essential basics.
- Basic: For all SMBs, providing protection against automated attacks.
- Important: For larger companies or those handling sensitive data, offering protection against common manual attacks.
- Essential: The highest level of security assurance, protecting against sophisticated attackers.
These levels make the framework easily adaptable for various organizations.
You can start at the initial level and progress to the desired level, with each level including key measures to help prioritize implementation.
Each measure is also mapped to a corresponding NIST CSF measure, ensuring partial implementation of NIST CSF as you adopt Cyberfundamentals measures.

But ... what are the next steps?
The Cyberfundamentals framework is extremely effective especially for Small and Medium enterprises as starting point where the ISO 27001 might seem a little bit to complex. Unlike other frameworks that can be overwhelming due to technical complexity,
Cyberfundamentals is user-friendly with its structured levels and key measures.
The CCB has developed a robust tool to improve cybersecurity in organizations, even outside Belgium, as the Cyberfundamentals is being adopted and accepted as proven and certifiable framework.
We guide you through the self-evaluation using the CCB’s tools and provide you with guidance to implement the security you need.
Contact us for further guidance.